Understanding the Virtual Private Cloud (VPC) components is key to learning how the networking works in the cloud. Keep in mind the cloud is a bunch of servers connected to the internet, and although you might think there is a weird magic behind it connecting all the dots, there is no magic, just a lot of cables, hardware and network configurations.
So let’s get started with a quick example:
When you start using Amazon Web Services, you have a default VPC in each AWS Region.
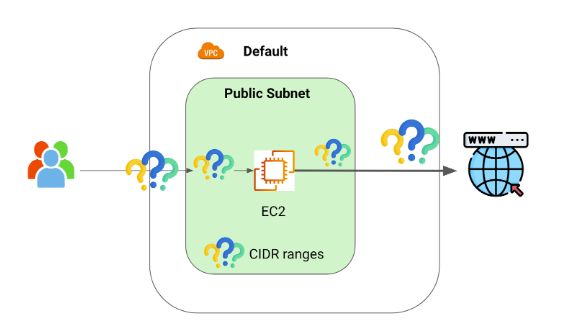
If we take a moment to understand this image, we have launched an EC2 instance in our Default VPC public subnet, but how are the users able to reach this instance? How is this instance being able to access the internet? How are the DNS resolution and the IP managed? Are there any firewalls?
A default VPC comes with a lot of components and configurations, so it’s easy to launch your applications. It can be a little bit tricky to remember them all since they have similar names and functionalities.
I’ve created a set of examples to go over them and hopefully by the end of this article you are able to understand most of them.
Let’s get started!
Subnets
When you create your AWS account, your default VPC comes with a Public subnet.
A subnet is a range of IP addresses. You launch AWS resources, such as Amazon EC2 instances, into your subnets. You can connect a subnet to the internet, other VPCs, and your own data centers.
Here, is good to know the difference between public and private:
Public subnet has a route to an Internet Gateway.
Private subnet doesn’t have a route to an Internet Gateway.
This is important in terms of security, you don’t want all your instances to have access to the internet, so make sure you are only exposing the things you need and route traffic internally.
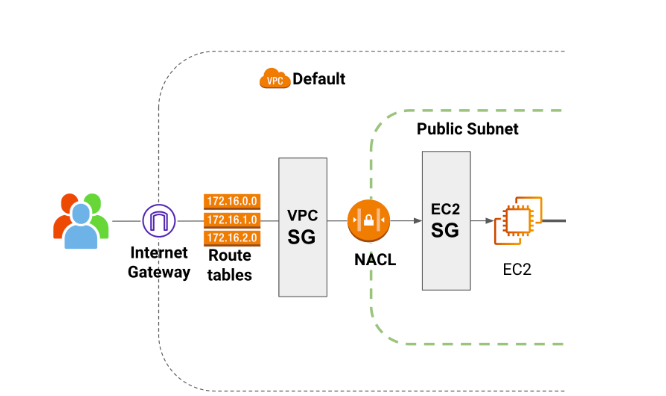
So let’s see our first part of our main picture. Here we can ask the question, how is the traffic managed from the internet to our VPC?
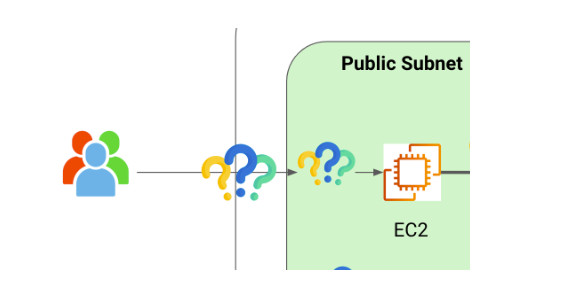
Internet Gateway
An internet gateway provides a target in your VPC route tables for internet-routable traffic.
Your VPC has an implicit router, and you use route tables to control where network traffic is directed.
Route Table
A route table is used to direct traffic in/out of a subnet. It contains a number of CIDRs (IP address ranges) and where to direct the appropriate traffic.
Think about it as a networking map that directs traffic from one location to another via the next hop. This creates a “route,” but it doesn’t filter traffic.
| Ok, so the traffic from the internet is directed to my VPC using the IP route table but does it go directly to my subnet or is there anything else in the middle? I expect some kind of firewall, is there any? The answer is yes, there is another component called NACL. |
NACL
A Network Access Control List (Network ACL, or NACL) is a firewall for a subnet.
Remember in AWS, a network ACL (or NACL) controls traffic to or from a subnet according to a set of inbound and outbound rules. This means, it represents network level security.
By default, it allows all inbound and outbound IPv4 traffic and, if applicable, IPv6 traffic.
But if you take another look at the image, something else is missing, you might be familiar with this one already, or you might have used it already. Yes we are talking about Security groups.
Security groups
A security group controls the traffic that is allowed to reach and leaves the resources that it is associated with. For example, after you associate a security group with an EC2 instance, it controls the inbound and outbound traffic for the instance.
All the following AWS services rely on Security Groups in some way:
- Amazon EC2 instances.
- AWS Lambda.
- AWS Elastic load balancing.
- Databases (Amazon RDS, Amazon Redshift)
- Other (ElastiCache, CloudSearch, Elastic Beanstalk, Elastic MapReduce)
- Container and Kubernetes services (ECS and EKS)
*Your VPC has a Security group as well. If you create a new VPC it will spin up a default security group whose initial settings deny all inbound traffic, allow all outbound traffic, and allow all traffic between instances assigned to the security group.
| Ok, so far we have introduced a lot of concepts that help you connect from the internet to your components inside the public VPC. Hopefully you have a better idea of some of the components that are involved. Before we continue, let’s refresh our initial picture. |
So, we have seen how to connect into our instances, but what happens on the other side? How do our instances connect to the outside world?
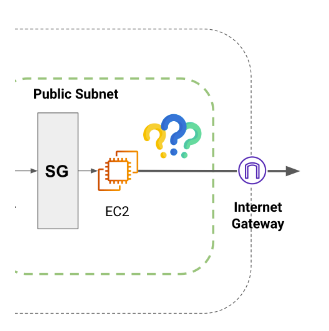
Well, we already introduced the Internet Gateway concept, which is the one that allows internet traffic (inbound and outbound) to our VPC? But, is it just that?
You might already have the answer based on all the things we already discussed, and yes, you might be right.
The same way you configured the inbound rules for your:
–Route Tables
-NACL
-Security Groups
You can configure the other way round. By default outbound rules might enable all traffic. You can easily check this, for example, on your EC2 instance security group.
Congrats! You reached the first step, before we continue, take a moment to review these concepts and play around on the AWS console.
If you have any questions, need expert guidance, or want to explore further, feel free to reach out to us here
